Cisco IOS XE devices can be onboarded in three different ways:
- PnP Connect: The Day 0 PnP Connect process discovers, installs, and provisions the Cisco IOS XE device to the SD-WAN overlay network.
- Bootstrap: In this scenario, the configuration is loaded onto a USB key that is inserted into the Cisco IOS XE device. The configuration file is created with vManage.
- Manual configuration: It is possible for a network administrator to connect to the console port to configure parameters.
SD-WAN Security
Cisco’s SD-WAN solution provides security for the management plane, control plane, and data plane. The control plane uses a Zero Trust model, the management plane uses role-based access control (RBAC) and access control lists (ACLs), and the data plane has integrated on-premises and cloud security layers.
The Cisco SD-WAN fabric incorporates a Zero Trust model in the control plane. As shown in Figure 11-2, all elements in the SD-WAN fabric are authenticated and authorized with each other prior to admission to the network. Digital certificates are used to establish secure Transport Layer Security 1.2 or Datagram Transport Layer Security (TLS/DTLS) control channels between vEdge routers and the controllers. TLS 1.2 is defined in RFC 5246. DTLS 1.2 is defined in RFC 6347. The hashing algorithm used in the control plane is SHA256, and the encryption algorithm is AES-256-GCM.
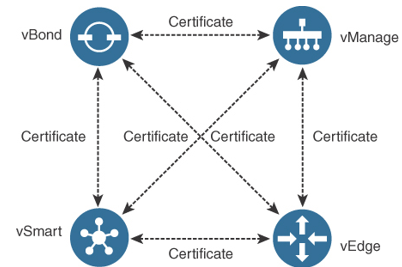
Figure 11-2 SD-WAN Certificate-Based Authentication
OMP and Network Configuration Protocol (NETCONF) run over these TLS/DLTS channels. OMP ensures the propagation of encryption keys used by the data plane. NETCONF allows the controllers to propagate configuration and networking information inside the control channel.
The vManage component uses RBAC to control the permission for users based on their privileges. RBAC controls who can access, read, and modify configurations and policies. Users are authenticated using authentication, authorization, and accounting (AAA) via SAML SSO, RADIUS, or TACACS.
vManage has some predefined user groups assigned with different levels of privileges:
- Basic group: Permissions to view interface and system information
- Operator group: Permission to view information
- Netadmin group: Permission to perform all operations
Remote access to the vManage server can be further controlled by using white-list access control lists (ACLs) to specify the only allowed IP subnets that can access the vManage server.
As mentioned earlier, vEdge routers use Advanced Encryption Standard (AES) with a 256-bit key length with the preferred operation Galois/Counter Mode (GCM)—hence AES-256-GCM. A secondary mode, cipher block chaining (CBC), can be used when required, such as in multicast applications.