Cisco ISE is a secure network access platform that enables control, visibility, and consistency for users and devices accessing the network. Within the SD-Access fabric, Cisco ISE provides all the identity and policy services. Cisco ISE is a critical component of SD-Access for policy enforcement; it allows for the dynamic mapping of users and endpoints to scalable groups, thereby simplifying the end-to-end security policy in the fabric. To support group-based policy end-to-end, Cisco TrustSec is leveraged to enable SGT information to be inserted into the VXLAN headers in the data plane traffic while also supporting multiple virtual networks (VNs). Cisco ISE supports AAA services, groups, policy, and endpoint profiling, and Cisco DNA Center orchestrates the policy workflows to use the functionality. The integration of ISE and DNA Center is done by establishing trust through ISE pxGRID services and by enabling External RESTful Services (ERS) to allow policies and contracts to flow between systems. Cisco DNA Center can create SGTs and send them to Cisco ISE via REST APIs.
Figure 10-6 illustrates the DNA Center and ISE integration using REST APIs and pxGRID.
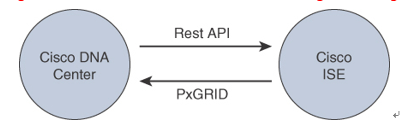
Figure 10-6 DNA Center and ISE Integration
A scalable group tag (SGT) consists of a 16-bit value contained in the VXLAN header. SGTs are also known as security groups. Cisco ISE manages the SGTs for a given SD-Access fabric. Although Cisco DNA Center drives the management of the policies, Cisco ISE is tightly integrated with DNA Center through REST APIs to provide the SGT information needed to enforce policy.
The deployment of Cisco ISE can occur through a standalone appliance or through a distributed set of appliances based on functionality.
TrustSec is a complementary enforcement technology that allows endpoint security management without the need to maintain access lists on all the network devices where the endpoints are connected. The ultimate goal of TrustSec is to assign an SGT to a user’s or device’s traffic at ingress (inbound into the network) and then enforce the access elsewhere in the infrastructure. The tag is assigned at login and enforced within the network (egress enforcement).
Each TrustSec design must have the following:
- SGT classification: ISE is used to classify devices based on authentication/authorization policies.
- SGT propagation: Propagation is done either inline or by using SGT Exchange Protocol (SXP).